The bot is a type of software application or script that executes on command, Botnet meaning is a collection of infected and Internet-connected devices, each of which is running one or more bots. Botnets can be used to perform Distributed Denial-of-Service (DDoS) attacks, steal data, send spam, and allow the attacker to take complete control remotely of an affected computer.
Browser Reconnaissance and Exfiltration via Adaptive Compression of Hypertext also known as Breach i.e security exploit against HTTPS when using HTTP compression. The minute a hacker effectively exploits a vulnerability in a computer or network device, and gains entree to its files and network.
Bring your own device (BYOD) policy refers to the movement of employees using their personal devices to connect to organizational networks and access systems and potentially sensitive or confidential data. Personal devices could include smartphones, personal computers, tablets, or USB drives. There are a number of BYOD MDM(mobile device management) tools available in the market these days.
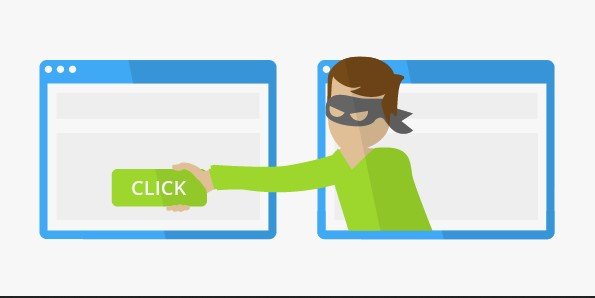
Clickjacking knew as User Interface redress attack or UI redress attack or UI redressing is a malicious technique of trapping a user into clicking on something different, thus possibly revealing confidential information or allowing hackers to take control of their machine while clicking on an unintended link or button.
“The cloud” refers to computing servers that are accessed via the Internet, and the application software and databases that run on those servers. Cloud servers are located in data centers all over the world. It’s a group of computers with large storage abilities that remotely fulfill requirements.
A distributed denial-of-service attack is a form of cyber-attack and one of the most powerful attacks on the internet. This attack is a malicious attempt to disturb the normal traffic of a target, service, or network by crushing the target or its infrastructure with a fake flood of Internet traffic.
An audio or video clip that has been amended and manipulated to seem real or believable. The most dangerous consequence of the popularity of deepfakes is that they can easily influence people into trusting a certain story or philosophy that may result in user-behavior with a bigger effect as in political or financial. Deepfakes can cause significant difficulties for commercial organizations.
A group of computers, printers, and peripherals that are interconnected and administered as a whole. For example, your computer is usually part of a domain at your workplace.
Encryption is a process that encodes a file or message so that it can only be accessed and read by authorized people only. Encryption uses an algorithm to encrypt, or scramble data and then uses a key for the receiving people to decrypt, or unscramble the message. It also helps to prevent theft by ensuring the data can only be accessed with a key.
An exploit is a malicious application, piece of software, or script, or sequence of commands that can be used to take advantage of a computer’s vulnerability to cause unintentional behavior to happen on computer software, hardware, or something electronic.
A Firewall is a network security device that filters incoming and outgoing network traffic based on an organization’s security policies. Firewalls can be hardware or software-based. A firewall is essentially the barrier that stands between a private network and the public Internet.
An Internet Protocol address is a numerical label assigned to every device connected to a computer network that uses the Internet Protocol address for communication. IP addresses are typically in the same format as a 32-bit number, display as four decimal numbers each with a range of 0 to 255, each set of three numbers is called an octet.
An umbrella term for a number of malicious software variants, including viruses, ransomware and spyware. Malware typically consists of code developed by computer cyberattackers, designed to cause extensive damage to data and information or to gain unauthorized access to a computer network
Pentesting is a short form for “penetration testing,” this security assessment is a means of evaluating security using hacking techniques and tools with the purpose of discovering vulnerabilities and evaluating security flaws. The main motive is to penetrate the web application or network security defenses by exploiting their vulnerabilities.
Ransomware is a form of malware that encrypts a victim’s file and deliberately prevents accessing files on a computer system holding data hostage. It will typically encrypt files and data, afterward for decryption or recovering they demand a ransom to be paid. For example, WannaCry Ransomware attacks. The top ransomware 2020 victims are Brookfield, Colorado, University of Utah. For removing ransomware attacks you need to install anti-ransomware or ransomware defenders.
Rootkit definition is malicious software that allows an unauthorized user to have privileged access to a computer system and to restricted areas of its application software or system software. It is a different kind of malware that allows cybercriminals to remotely access and control your computer systems. Rootkits are hard to detect, making it likely that this type of malware could live on your computer system for a long time and give unauthorized access to hackers.
Social engineering is a technique used to manipulate and betray people to gain sensitive and personal information. Spear phishing social engineering is a kind of attack that sending emails apparently from a trusted sender to make targeted individuals reveal confidential information. Once a hacker understands what person’s actions, they can recover exactly what they’re looking for – like financial data and passwords.
Software is a set of programs that tell a computer to perform a task. These instructions are compiled into a exe package that can install and use after installation on a computer system. Microsoft Office is application software and the Operating system is the system software. Adobe acrobat dc, adobe acrobat, avg secure VPN, team viewer 8 are the kind of best examples of software.
Spear phishing or phishing is a technique used by hackers to gain sensitive information. The main motive is to either infect devices with malware or influence victims to hand over information or money. This is the most effective form of acquiring confidential information on the internet, accounting for 91% of cyberattacks. An example of spear phishing is using phishing email messages designed to hoax people into revealing personal or confidential data such as passwords and bank account information.
Computer spyware in cybersecurity refers to a kind of software program that “spies” on what end-users do with their computers online or offline. Through this close monitoring, computer spyware gathers information about the user and sends collected information over the WWW i.e., World Wide Web for an anonymous person’s or an organization’s benefit. This is usually done without that user’s knowledge. Spybot and Ad-Aware are two of the highly recommended programs for safe spyware removal software. These tools are free and paid available on the internet named as internet spyware or anti-spyware tools.
Trojan horse malware is a program designed to breach the security of a computer system while apparently performing some harmless function. Also in layman’s term trojan in cybersecurity, is a piece of malware that often allows a hacker to gain remote access to a computer through a “back door”. Avast, Avg, trojan remover are the popular trojan antiviruses available on the internet.
A VPN (virtual private network) is a method to use a public telecommunication set-up, such as the Internet, to provide remote offices or specific users with protected access to their organization’s network. A VPN concentrator is one of the popular vpn hardware device and cisco anyconnect windows 10 and cisco anyconnect linux is the best software based VPN available.
The virus is a type of malware whose aim is to corrupt, erase or modify information on a computer system before spreading to others systems. The shortcut virus is a very common computer virus that hides your files and changes them with shortcuts with the same file name. When you click on the shortcuts, the virus replicates itself and additional infects your drive. The shortcut virus usually come in your drive via running a .exe file that limited the virus or from using a flash drive on multiple computers.
In cybersecurity terms, the differences in hacker “hats” refers to the motive of the hacker. For example:
White hat: A white hat is an ethical computer hacker, or a computer security expert, who Breaches the network to gain sensitive information with the owner’s consent is making it completely authorized and specializes in penetration testing and in additional testing methodologies that ensures the security of an organization’s information computer systems.
Black hat: Black Hat hackers are those who break into the network to steal information that will be used to harm the owner or the users without owner’s consent. Black hat Europe is entirely illegal.
A computer worm is standalone malware computer program can replicate itself without any human interaction, and it does not need to bind itself to a software application program in order to cause damage.

























2 Replies to “Top 25 Cyber Security Titles For Those Uses A Computer Should Know”