What is Fonix Ransowmare? How we can remove it?
Fonix Ransomware is also known as FonixCrypter and Xinof, tossed in June 2020 but increased its quantity of victims significantly in November 2020. Cybercriminals used both names, and encrypted data files were renamed with either extension, .fonix or .xinof. Fonix Ransomware is very aggressive as by the data analyst teams. Fonix working under a ransomware-as-a-service (RaaS) model, leaving users to complete the real ransomware attacks.
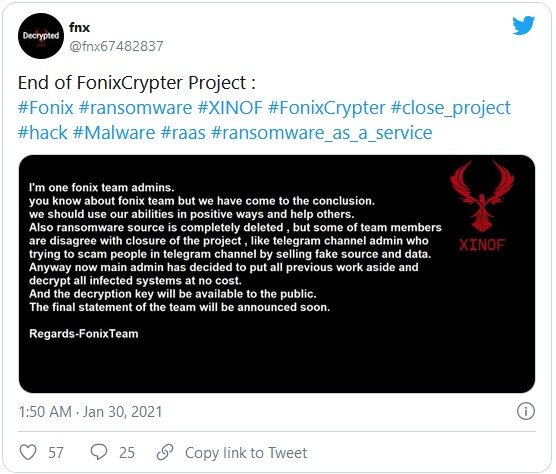
One of the Fonix ransomware admins “tweeted” that they have to to pull down the ransomware action.
“I’m one fonix team admins.
you know about fonix team but we have come to the conclusion.
we should use our abilities in positive ways and help others.Also, ransomware source is completely deleted, but some of team members are disagree with closure of the project, like telegram channel admin who trying to scam people in telegram channel by selling fake source and data.
Anyway, now main admin has decided to put all previous work aside and decrypt all infected systems at no cost. And the decryption key will be available to the public.
The final statement of the team will be announced soon”
Regards – FonixTeam
How to protect against ransomware?
Fonix is no longer problematic; however, other ransomware strains are extra dynamic than ever in 2021. Our piece of information for remaining safe is still much the similar:
- Beware of e-mails with attachments;
- Do not execute/run files gain from unconfirmed sources;
- Use security solutions on all devices that have Internet access;
- Create and safeguard backup copies of all critical data on other devices
Read Also: How to Launch Paros Proxy GUI in Kali Linux 2021?
How to decrypt encrypted files with Kaspersky ransomware decryptor “RakhniDecryptor”?
If you have been infected with the FonixRansomware, you can decrypt your affected files for free using an updated version of Kaspersky’s RakhniDecryptor. Kaspersky has introduced a Kaspersky ransomware decryptor for the Fonix Ransomware also known as XONIF that permits victims to recover their encrypted files for free of cost. RakhniDecryptor decrypt files encrypted by the Fonix ransomware, also allows victims of ransomware attacks to decrypt files affected by types of ransomware strain like Agent.iih, Aura, Autoit, Bitman (TeslaCrypt) version 3 and 4, Chimera, Cryptokluchen, Crysis (versions 2 and 3), Democry, Dharma, FortuneCrypt. Jaff, Lamer, Lortok, new versions of Cryakl ransomware, Pletor, Rakhni, Rotor and Yatron,
You can also use Kaspersky’s RakhniDecryptor “The ransomware defender” in case your system is attacked by the following the ransomware
- Trojan-Ransom.Win32.Fonix
- Trojan-Ransom.Win32.Rakhni
- Trojan-Ransom.Win32.Agent.iih
- Trojan-Ransom.Win32.Autoit
- Trojan-Ransom.Win32.Aura
- Trojan-Ransom.AndroidOS.Pletor
- Trojan-Ransom.Win32.Rotor
- Trojan-Ransom.Win32.Lamer
- Trojan-Ransom.Win32.Cryptokluchen
- Trojan-Ransom.Win32.Democry
- Trojan-Ransom.Win32.GandCrypt ver. 4 and 5
- Trojan-Ransom.Win32.Bitman ver. 3 and 4
- Trojan-Ransom.Win32.Libra
- Trojan-Ransom.MSIL.Lobzik
- Trojan-Ransom.MSIL.Lortok
- Trojan-Ransom.MSIL.Yatron
- Trojan-Ransom.Win32.Chimera
- Trojan-Ransom.Win32.CryFile
- Trojan-Ransom.Win32.Crypren.afjh (FortuneCrypt)
- Trojan-Ransom.Win32.Nemchig
- Trojan-Ransom.Win32.Mircop
- Trojan-Ransom.Win32.Mor
- Trojan-Ransom.Win32.Crusis (Dharma)
- Trojan-Ransom.Win32.AecHu
- Trojan-Ransom.Win32.Jaff
- Trojan-Ransom.Win32.Cryakl CL 1.0.0.0
- Trojan-Ransom.Win32.Cryakl CL 1.0.0.0.u
- Trojan-Ransom.Win32.Cryakl CL 1.2.0.0
- Trojan-Ransom.Win32.Cryakl CL 1.3.0.0
- Trojan-Ransom.Win32.Cryakl CL 1.3.1.0
Read Also: How to Create Rescue Disk With Kaspersky Rescue Disk 2021?
How to install kaspersky’s rakhnidecryptor ransomware decryptor?
Step 1.
Download rakhnidecryptor ransomware decryptor from RakhniDecryptor.zip and extract the files from it
Step 2.
Open the folder with the extracted files.
Step 3.
Run the RakhniDecryptor.exe.
Step 4.
In the Kaspersky ransomware decryptor, RakhniDecryptor application window click the Change parameters link
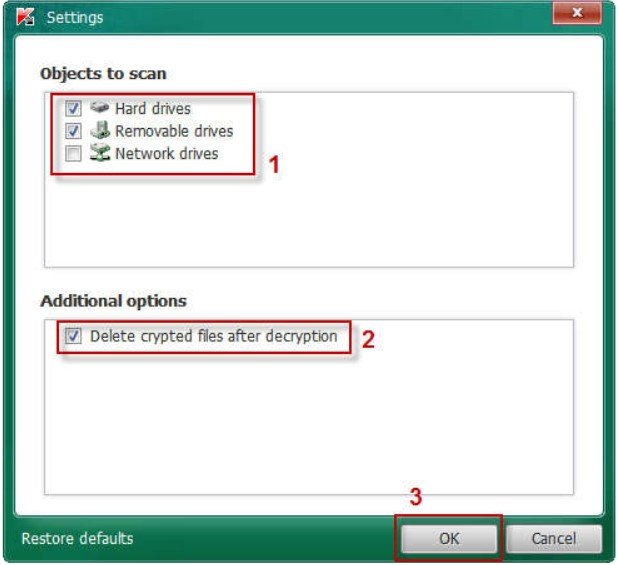
Step 5.
In the Settings window select the objects to scan (hard drives/removable drives/network drives). Select the checkbox “Delete crypted files after decryption” and click OK
Step 6.
Click Start scan.
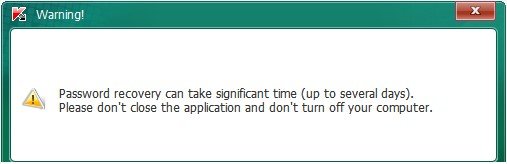
Step 7.
The application will start recovering the password. Its popups the Warning! window message.
Note* Do not exit the program or shut down the computer until the utility is done with decrypting all the file data *




3 Replies to “Are You Looking For Defence Against FonixCrypter Ransomware 2021?”