Encryption and decryption
Data that can be read and understood without any unusual measures is called plaintext or cleartext. The technique of disguising plaintext in such a way as to hide its matter is called encryption. Encrypting plaintext outcomes in unreadable gibberish called ciphertext. You use encryption to ensure that information is hidden from someone for whom it is not intended, even those who can get the encrypted data. The procedure of reverting ciphertext to its original plaintext is called decryption.
What is cryptography?
Cryptography is the art of using mathematics to encrypt and decrypt data. Cryptography enables you to store sensitive information or transmit it across insecure networks so that it cannot be read by anybody except the intended receiver. While cryptography is the art of securing data, cryptanalysis is the art of analyzing and breaking secure communication. Classical cryptanalysis includes an interesting combination of analytical reasoning, application of mathematical tools, pattern finding, patience, determination, and luck. Cryptanalysts are also called attackers. Cryptology embraces both cryptography and cryptanalysis
Strong cryptography
“There are two kinds of cryptography in this world: cryptography that will stop your kid sister from reading your files, and cryptography that will stop major governments from reading your files. This book is about the latter.”
–Bruce Schneier, Applied Cryptography: Protocols, Algorithms, and Source Code in C.
Cryptography can major areas of strength for be frail, as made sense of above. Cryptographic strength is estimated in the time and assets it would expect to recuperate the plaintext. The consequence of solid cryptography is ciphertext that is extremely challenging to translate without ownership of the fitting disentangling device. How troublesome? All considering the present processing power and accessible time — even a billion PCs doing a billion really looks at a second — unraveling the consequence of solid cryptography before the finish of the universe is beyond the realm of possibilities. One would think, then, at that point, areas of strength for that would hold up fairly well against even an incredibly resolved cryptanalyst. Who’s truly to say? Nobody has demonstrated that the most grounded encryption possible today will hold up under the upcoming registering power. Be that as it may, areas of strength for the utilized by PGP is the most ideal that anyone could hope to find today. Cautiousness and traditionalism will safeguard you better, in any case, than cases of solidness.
How does cryptography work?
A cryptographic algorithm, or cipher, is a numerical capability utilized in the encryption and decoding process. A cryptographic algorithm works in combination with a key— a word, number, or expression—to encrypt the plaintext. The equivalent plaintext encodes to various ciphertext with various keys. The security of encrypted data is entirely dependent on two things: the strength of the cryptographic algorithm and the secrecy of the key. A cryptographic algorithm, plus all possible keys and all the protocols that make it work comprise a cryptosystem. PGP is a cryptosystem.
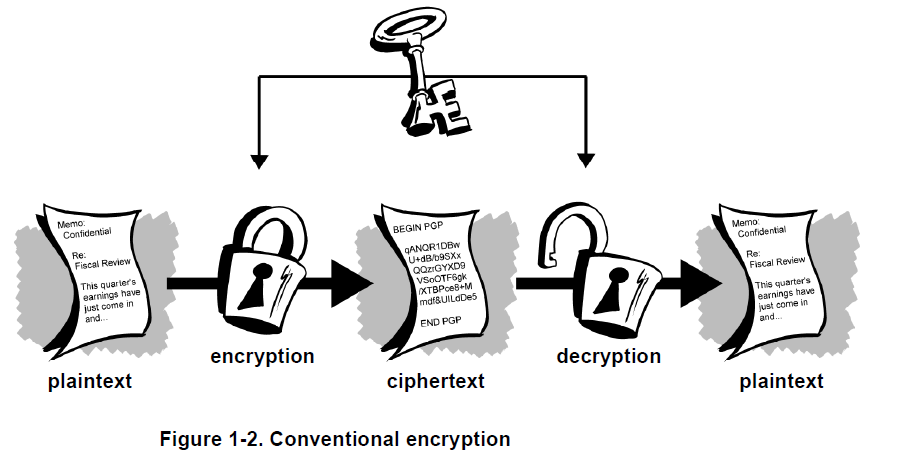
Conventional cryptography
In conventional cryptography, also called secret-key or symmetric-key encryption, one key is used both for encryption and decryption. The Data Encryption Standard (DES) is an example of a conventional cryptosystem that is widely employed by the Federal Government
Caesar’s Cipher
An extremely simple example of conventional cryptography is a substitution cipher. A substitution cipher substitutes one piece of information for another. This is most frequently done by offsetting letters of the alphabet. Two examples are Captain Midnight’s Secret Decoder Ring, which you may have owned when you were a kid, and Julius Caesar’s cipher. In both cases, the algorithm is to offset the alphabet and the key is the number of characters to offset it.
Key management and conventional encryption
Conventional encryption has benefits. It is very fast. It is especially useful for encrypting data that is not going anywhere. However, conventional encryption alone as a means for transmitting secure data can be quite expensive simply due to the difficulty of secure key distribution.
For a sender and recipient to communicate securely using conventional encryption, they must agree upon a key and keep it secret between themselves. If they are in different physical locations, theymust trust a courier, the Bat Phone, or some other secure communication medium to prevent the disclosure of the secret key during transmission.
Public key cryptography
The problems of key distribution are solved by public key cryptography, the concept of which was introduced byWhitfield Diffie and Martin Hellman in 1975.
Public key cryptography is an asymmetric scheme that uses a pair of keys for encryption: a public key, which encrypts data, and a corresponding private, or secret key for decryption. You publish your public key to the worldwhile
keeping your private key secret.Anyone with a copy of your public key can then encrypt information that only you can read. Even people you have never met.
The primary benefit of public key cryptography is that it allows people who have no preexisting security arrangement to exchange messages securely. The need for sender and receiver to share secret keys via some secure channel is eliminated; all communications involve only public keys, and no private key is ever transmitted or shared.