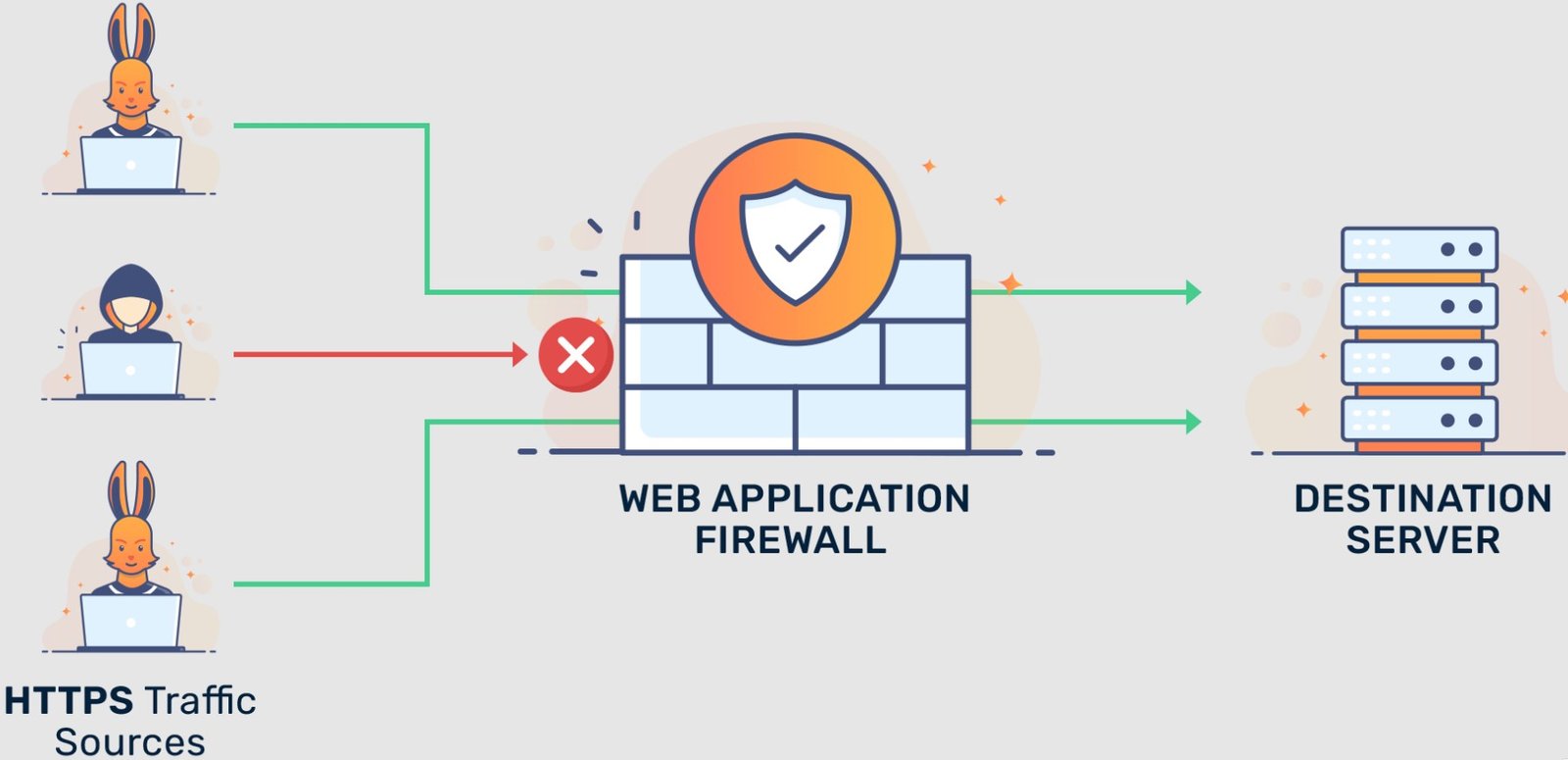
What is WAF?
A web application firewall (WAF) is a security tool that monitors and controls incoming and outgoing traffic to and from web applications. Its main purpose is to protect web applications from various types of cyberattacks such as SQL injection, cross-site scripting (XSS), and cross-site request forgery (CSRF).
A WAF can be deployed as a hardware appliance, virtual appliance, or cloud-based service. It uses a combination of signature-based and behaviour-based detection methods to identify and block malicious traffic. Signature-based detection uses a predefined set of rules to match known attack patterns, while behaviour-based detection uses machine learning algorithms to identify and block traffic that deviates from normal behaviour.
WAFs can also be configured to enforce security policies and compliance regulations, such as PCI-DSS. Some WAFs also include additional features such as DDoS protection, SSL/TLS encryption inspection, and advanced bot protection.
What is the difference between blocklist & allowlist WAFs?
Web application firewalls (WAFs) can be configured to use either a blocklist or an allowlist approach to protect web applications.
A blocklist-based WAF, also known as a “blacklist” WAF, blocks all incoming traffic by default and only allows traffic that is specifically permitted through a list of known “good” IP addresses and/or user agents. The idea behind this approach is that by blocking all traffic by default, the WAF can prevent any malicious traffic from reaching the web application.
On the other hand, an allowlist-based WAF, also known as a “whitelist” WAF, allows all incoming traffic by default and only blocks traffic that is specifically prohibited through a list of known “bad” IP addresses and/or user agents. The idea behind this approach is that by allowing all traffic by default, the WAF can permit legitimate traffic to reach the web application and only block malicious traffic.
Both approaches have their own advantages and disadvantages. The blocklist approach can provide a higher level of security by blocking all traffic by default, but it can also lead to false positives and block legitimate traffic. The allowlist approach can provide a lower level of security by allowing all traffic by default, but it can also allow malicious traffic to reach the web application.
Don’t Miss:
- Splunk vs ArcSight
- What is difference between Ubuntu vs Kali Linux
- The Best Linux Distros for Programming in 2023
- The Best Linux for Gaming in 2023
- Best Decryption Tools and Methods
- People Should Learn How To Use Decryption
- Understand the Types of Decryption – Symmetric, Asymmetric
- What is decryption? Importance of decryption in today’s world
- How to change the hostname on Linux
- 10 Reasons Why Linux is the Future of Computing
Network-based, Host-based, and Cloud-based WAFs
Network-based WAFs:
These are deployed at the network perimeter, typically in front of a web server, and inspect all incoming traffic to the web application. They can be physical or virtual appliances and are placed in-line with the traffic flow. The main advantage of network-based WAFs is that they can protect the web application from various types of attacks, including those that originate from outside the network.
Host-based WAFs:
These are deployed on the same server as the web application, and inspect traffic that is directed to the web application on that server. The main advantage of host-based WAFs is that they can provide a higher level of security by inspecting all traffic that is directed to the web application, including that which originates from within the network.
Cloud-based WAFs:
These are deployed in the cloud, and protect web applications that are hosted in the cloud. These can be used to protect web applications that are running in a public, private or hybrid cloud environments. The main advantage of cloud-based WAFs is that they can be easily scaled to accommodate large numbers of users and requests, and they can also be used to protect web applications that are hosted in multiple locations
Don’t Miss:
- Splunk vs ArcSight
- What is difference between Ubuntu vs Kali Linux
- The Best Linux Distros for Programming in 2023
- The Best Linux for Gaming in 2023
- Best Decryption Tools and Methods
- People Should Learn How To Use Decryption
- Understand the Types of Decryption – Symmetric, Asymmetric
- What is decryption? Importance of decryption in today’s world
- How to change the hostname on Linux
- 10 Reasons Why Linux is the Future of Computing